Tunneling?
In networking, tunnels are a method for transporting data across a network using protocols that are not supported by that network. In other words, tunneling is a mechanism provided to transfer data securely between two networks.
Tunneling works by encapsulating packets: wrapping packets inside of other packets. Tunneling is often used in virtual private networks (VPNs). It can also set up efficient and secure connections between networks, enable the usage of unsupported network protocols, and in some cases allow users to bypass firewalls.
What are voluntary and compulsory tunnels?
Voluntary Tunneling
Users computer is an end point of the tunnel and acts as tunnel client. Here the client or user issues a request to configure and create a voluntary tunnel. They require a dial up or LAN connection. Example of dial up connection is internet at home where a call is made to the ISP and connection is obtained.
Compulsory tunneling
In compulsory tunneling, instead of the user a vpn remote access server configures and creates a tunnel. Hence, the end point is the Remote sever not the user.
Explain static and dynamic tunnels
Static Tunnel
The manually created tunnels are called Static Tunnels. Static tunnels creation is the only choice when global discovery of hosts and tunnel partners are disabled by enhancing express tunnels into manually created tunnels. The priority is higher when compared with static tunnel.
Dynamic Tunnel
The tunnels that are auto-discovered are known as dynamic tunnels. Dynamic tunnels are created quickly and automatically after the Packet Shaper is reset. At the time of preventing automatic tunnel, dynamic tunnels are allowed to setup the situation.
VPN tunnel
A VPN is a secure, encrypted connection over a publicly shared network. Tunneling is the process by which VPN packets reach their intended destination, which is typically a private network.
VPN
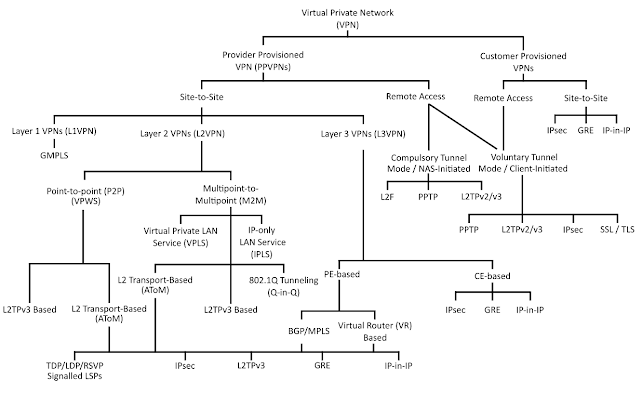
A virtual private network (VPN) is a secure connection over an unsecure network, such as the internet. The encrypted connection helps ensure that sensitive data is safely transmitted. The term “virtual private network” implies that the network is accessible by users sitting in the remote area. It uses tunneling protocols to create a secure connection.
What are the different types of VPN?
Remote Access VPN
Access VPN is used to provide connectivity to remote users such as laptops, tablets, or smartphones and telecommuters. Advances in VPN technology have allowed security checks to be conducted on endpoints to make sure they meet a certain posture before connecting.
It serves as an alternative to dial-up connections or ISDN (Integrated Services Digital Network) connections. It is a low-cost solution and provides a wide range of connectivity.
PPTP-
PPTP or Point-to-Point Tunneling Protocol generates a tunnel and confines the data packet. Point-to-Point Protocol (PPP) is used to encrypt the data between the connection. PPTP is one of the most widely used VPN protocol and has been in use since the early release of Windows. PPTP is also used on Mac and Linux apart from Windows.
L2TP-
L2TP or Layer 2 Tunneling Protocol is a tunneling protocol that is often combined with another VPN security protocol like IPSec to establish a highly secure VPN connection. L2TP generates a tunnel between two L2TP connection points and IPSec protocol encrypts the data and maintains secure communication between the tunnel.
Openvpn-
OpenVPN is an open source VPN that is commonly used for creating Point-to-Point and Site-to-Site connections. It uses a traditional security protocol based on SSL and TLS protocol.
SSTP-
Secure Socket Tunneling Protocol is popular due to its full integration with every Microsoft operating system since Windows Vista SP 1. SSTP utilizes 2048-bit SSL/TLS certificates for authentication and 256-bit SSL keys for encryption. The biggest drawback to SSTP is that is basically a Microsoft-developed proprietary protocol and developers do not have access to the underlying code.
TL;DR: good security, difficult to block and detect, great support for native and third party clients
Site-to-Site VPN
A Site-to-Site or Router-to-Router VPN is commonly used to connect the corporate network of one office to another branch in different locations.
There are 2 sub-categories as mentioned below:
- Intranet VPN: Intranet VPN is useful for connecting remote offices in different geographical locations using shared infrastructure (internet connectivity and servers) with the same accessibility policies as a private WAN (wide area network).
- Extranet VPN: Extranet VPN uses shared infrastructure over an intranet, suppliers, customers, partners, and other entities and connects them using dedicated connections.
EoIP-
EoIP tunnel (Ethernet over IP) is a Datalink layer tunnel (L2 of the OSI model) over the network layer (L3). Data is transmitted through this tunnel at the Ethernet frame level. EoIP provides a transparent network environment that emulates a direct Ethernet connection between networks.
Layer 3 VPN: Both branches have different network IP blocks. For Example-
GRE-
Generic Routing Encapsulation is a tunneling protocol developed by Cisco Systems that can encapsulate a wide variety of network layer protocols inside virtual point-to-point links or point-to-multipoint links over an Internet Protocol network.
The advantage of GRE over other tunneling protocols is that it can encapsulate broadcast, multicast traffic (multicast streaming or routing protocols) or other non-IP protocols. GRE packets can be protected by using Internet Protocol Security (IPSec) ensuring confidentiality and integrity of the tunneled traffic.
IPIP-
An IP Tunnel is a communication channel, that can be created by using encapsulation technologies, between two networks that do not have a routing path. Every IP packet that is shared between the two networks is encapsulated within another packet and then sent via the tunnel.
IPSEC-
Internet Protocol Security, known as IPSec, is used to secure Internet communication across an IP network. IPSec secures Internet Protocol communication by verifying the session and encrypts each data packet during the connection.
IPSec runs in 2 modes:
(i) Transport mode
(ii) Tunneling mode
The work of transport mode is to encrypt the message in the data packet and the tunneling mode encrypts the whole data packet. IPSec can also be used with other security protocols to improve the security system.
VPLS: point to multipoint. The virtual private LAN service (VPLS) is an Ethernet-based point-to-multipoint Layer 2 virtual private network (VPN) that enables you to connect geographically dispersed Ethernet local area network (LAN) sites to each other across an MPLS backbone.
*****




0 Comments